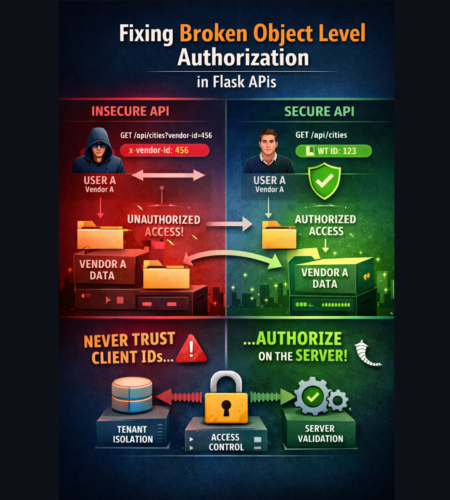
Broken Object Level Authorization (BOLA) is an API security vulnerability where an authenticated user can access or modify data they do not own because the API fails to enforce authorization at the object level.
BOLA typically occurs when backend services trust client-supplied identifiers—such as vendor_id or account_id—instead of deriving identity from authenticated context.
This article explains what BOLA is, why it is dangerous in multi-tenant Flask APIs, and how to fix it using secure, server-side authorization patterns.
TL;DR: Broken Object Level Authorization (BOLA) occurs when APIs trust client-supplied object IDs, allowing users to access data they do not own. The correct fix is to derive identity from authentication context and enforce object-level authorization server-side for every request.
What is Broken Object Level Authorization (BOLA)?
Broken Object Level Authorization (BOLA) is a vulnerability that allows users to access objects they are not authorized to access due to missing or improper authorization checks.
In APIs, this usually happens when developers rely on object identifiers provided in request headers, query parameters, or request bodies without verifying that the authenticated user owns or is permitted to access those objects.
BOLA is also known as IDOR (Insecure Direct Object Reference) and is ranked #1 in the OWASP API Security Top 10 (2023).
Why is Broken Object Level Authorization dangerous in APIs?
BOLA is dangerous because it breaks tenant isolation and exposes sensitive data across users or organizations.
In multi-tenant systems, a single BOLA flaw can allow:
- One tenant to view another tenant’s confidential data
- Unauthorized modification or deletion of resources
- Regulatory compliance violations (GDPR, CCPA)
- Severe reputational damage to the platform
Because BOLA exploits valid authentication, it is often harder to detect than unauthenticated attacks.
How do attackers exploit BOLA vulnerabilities?
Attackers exploit BOLA by manipulating object identifiers in API requests.
For example:
- Changing
vendor_idin a query string - Modifying
x-vendor-idheaders - Guessing or enumerating numeric or UUID-based object IDs
If the API does not validate ownership, the backend will return or modify data belonging to another user or tenant.
What is a real example of a BOLA vulnerability?
Below is a vulnerable Flask pattern that demonstrates BOLA.
Vulnerable Example (Do Not Use)
def get_vendor_id():
return (
request.headers.get("x-vendor-id")
or request.args.get("vendor_id")
)
@app.get("/api/serviceareas/cities")
def list_cities():
vendor_id = get_vendor_id()
return fetch_cities_for_vendor(vendor_id)
Why this is vulnerable
- The API trusts client-supplied identifiers
- Any authenticated user can impersonate another vendor
- No ownership validation exists
How do you fix BOLA in Flask APIs?
You fix BOLA by deriving object ownership from authentication context, not from client input.
Secure Strategy
- Authenticate the user using JWT or session-based auth
- Extract tenant or vendor identity from the token
- Enforce authorization server-side
- Ignore all client-supplied tenant identifiers
Secure Flask Implementation (BOLA-Safe)
Authentication Decorator
from functools import wraps
from flask import request, jsonify, g
import jwt
SECRET_KEY = "super-secret-key"
def require_auth(fn):
@wraps(fn)
def wrapper(*args, **kwargs):
auth = request.headers.get("Authorization", "")
if not auth.startswith("Bearer "):
return jsonify({"error": "Unauthorized"}), 401
token = auth.split(" ", 1)[1]
try:
payload = jwt.decode(token, SECRET_KEY, algorithms=["HS256"])
except jwt.PyJWTError:
return jsonify({"error": "Invalid token"}), 401
g.user = {
"vendor_id": payload.get("sub"),
"role": payload.get("role")
}
if not g.user["vendor_id"]:
return jsonify({"error": "Unauthorized"}), 401
return fn(*args, **kwargs)
return wrapper
Secure Endpoint Example
@app.get("/api/serviceareas/cities")
@require_auth
def list_cities():
vendor_id = g.user["vendor_id"]
return fetch_cities_for_vendor(vendor_id)
Why this works
- Vendor identity comes from a trusted JWT
- Client cannot override ownership
- Tenant isolation is enforced consistently
What are best practices to prevent BOLA vulnerabilities?
- Never trust client-supplied object identifiers
- Always derive ownership from authentication context
- Scope database queries by tenant ID
- Enforce authorization before data access
- Add automated tests for cross-tenant access
- Log and audit privileged (admin) access
How do you test APIs for BOLA vulnerabilities?
You test for BOLA by attempting unauthorized object access.
Manual Testing
- Authenticate as User A
- Modify object IDs to reference User B’s resources
- Verify the API denies access
Automated Testing
- Write tests that attempt cross-tenant access
- Ensure responses return
403 Forbiddenor404 Not Found - Test all CRUD endpoints
Frequently Asked Questions about Broken Object Level Authorization
What is Broken Object Level Authorization (BOLA)?
Broken Object Level Authorization is a vulnerability where APIs allow users to access or modify objects they do not own due to missing authorization checks.
Is BOLA the same as IDOR?
Yes. BOLA is the modern API-focused term for IDOR (Insecure Direct Object Reference).
Why is BOLA considered a critical vulnerability?
BOLA enables unauthorized data access across users or tenants, leading to data breaches and compliance violations. It is ranked #1 in the OWASP API Security Top 10 (2023).
What causes BOLA vulnerabilities in Flask APIs?
BOLA occurs when Flask APIs trust identifiers provided in headers, query parameters, or request bodies instead of authenticated user context.
How do you prevent BOLA in Flask APIs?
Prevent BOLA by extracting identity from authentication tokens, enforcing server-side authorization, and ignoring all client-supplied object identifiers.
How can you test for BOLA vulnerabilities?
Test for BOLA by attempting to access or modify another user’s resources by changing object IDs and confirming access is denied.
Final Takeaway
Broken Object Level Authorization occurs when APIs trust client-controlled identifiers.
The correct fix is simple and consistent: authenticate users, derive identity from trusted context, and enforce authorization on the server for every object access.
Comments